What Lurks Beneath the Cloud: Unveiling the Security Risks of Cloud Computing
Data Breaches and Unauthorized Access
Cloud computing systems often house vast amounts of sensitive data, making them a lucrative target for cybercriminals. Vulnerabilities in cloud security can lead to data breaches, where unauthorized individuals gain access to confidential information, potentially resulting in financial losses, reputational damage, and legal consequences.
Exploiting Cloud Vulnerabilities
Attackers employ various techniques to exploit cloud vulnerabilities and gain unauthorized access to data. These include:
- Misconfigurations: Improperly configured cloud resources, such as storage buckets or databases, can expose data to unauthorized users.
- Weak Credentials: Using weak or easily guessable passwords or API keys can allow attackers to compromise cloud accounts.
- Phishing Attacks: Attackers send deceptive emails or messages to trick users into revealing their cloud credentials or clicking malicious links that install malware.
- Malware Infections: Malware, such as viruses, trojans, and ransomware, can infect cloud workloads and exfiltrate data or provide attackers with backdoor access.
- DDoS Attacks: Distributed Denial-of-Service (DDoS) attacks can overwhelm cloud resources, causing service disruptions and potentially exposing data.
High-Profile Data Breaches
Several high-profile data breaches have occurred due to cloud security lapses, including:
- Capital One: In 2019, a misconfigured cloud storage bucket exposed the personal information of over 100 million Capital One customers.
- Marriott International: In 2018, a malware infection compromised the reservation system of Marriott International, exposing the personal information of over 500 million guests.
- Equifax: In 2017, a vulnerability in Equifax’s web application allowed attackers to access the personal information of over 145 million consumers.
Insecure Interfaces and APIs

In cloud computing, insecure interfaces and APIs pose significant security risks. APIs (Application Programming Interfaces) serve as gateways for communication between different applications and services, while interfaces provide a means for users to interact with cloud-based resources. When these components lack adequate security measures, they can become entry points for attackers to exploit vulnerabilities and compromise data or systems.
Best Practices for Designing Secure APIs and Interfaces
To mitigate the risks associated with insecure interfaces and APIs, cloud providers and developers should adhere to best practices, including:
- Authentication and Authorization: Implement robust authentication and authorization mechanisms to control access to APIs and interfaces. This can include multi-factor authentication, role-based access control, and token-based authentication.
- Input Validation: Validate user input thoroughly to prevent malicious inputs from exploiting vulnerabilities. This includes validating data types, lengths, and formats.
- Encryption: Encrypt data in transit and at rest to protect it from unauthorized access. This ensures that even if data is intercepted, it remains confidential.
- Regular Updates and Patching: Regularly update and patch APIs and interfaces to address newly discovered vulnerabilities. This includes applying security patches and updates promptly.
- Least Privilege: Grant users only the minimum level of access necessary to perform their tasks. This reduces the risk of unauthorized access to sensitive data or resources.
Comparison of Security Features and Vulnerabilities of Different Cloud API Protocols
Different cloud API protocols offer varying levels of security features and vulnerabilities. The following table provides a comparison of some common protocols:
| Protocol | Security Features | Vulnerabilities |
|---|---|---|
| REST (Representational State Transfer) | – Simple and widely adopted
|
– Prone to cross-site scripting (XSS) and injection attacks
|
| SOAP (Simple Object Access Protocol) | – XML-based protocol
|
– More complex than REST
|
| gRPC (Google Remote Procedure Call) | – High performance
|
– Relatively new protocol
|
Shared Responsibility Model
Cloud computing introduces a unique security paradigm known as the shared responsibility model, which Artikels the division of responsibilities between cloud providers and customers in securing cloud environments.
This model defines the boundaries of each party’s accountability in safeguarding data, applications, and infrastructure.
The cloud provider is primarily responsible for securing the underlying infrastructure, including physical security, network security, and the virtualization layer. They are also responsible for implementing security measures to protect the cloud platform itself, such as firewalls, intrusion detection systems, and access controls.
Customers, on the other hand, are responsible for securing their own data, applications, and operating systems within the cloud environment. This includes implementing security controls such as encryption, access management, and security monitoring. They are also responsible for ensuring that their applications and data comply with relevant security regulations and standards.
Division of Responsibilities
The division of responsibilities in the shared responsibility model can be further illustrated through specific scenarios:
- Infrastructure Security: The cloud provider is responsible for securing the physical infrastructure, including data centers, servers, and network devices. They are also responsible for implementing security measures to protect the cloud platform itself, such as firewalls, intrusion detection systems, and access controls.
- Data Security: Customers are responsible for securing their own data stored in the cloud. This includes implementing encryption, access controls, and security monitoring to protect data from unauthorized access, modification, or deletion.
- Application Security: Customers are responsible for securing their applications deployed in the cloud. This includes implementing security controls such as input validation, error handling, and secure coding practices to prevent vulnerabilities that could be exploited by attackers.
- Compliance and Regulatory Requirements: Customers are responsible for ensuring that their applications and data comply with relevant security regulations and standards. This may include industry-specific regulations, such as HIPAA or PCI DSS, or general data protection regulations, such as GDPR.
Potential Security Implications
The shared responsibility model can introduce potential security implications for both cloud providers and customers:
- Misconfiguration: Customers may inadvertently misconfigure their cloud resources, exposing them to security vulnerabilities. This can occur due to a lack of expertise, misinterpretation of documentation, or human error.
- Lack of Visibility: Cloud providers may have limited visibility into customer environments, making it difficult to detect and respond to security incidents. This can be a challenge, especially in multi-tenant cloud environments where multiple customers share the same infrastructure.
- Compliance Challenges: Customers may struggle to maintain compliance with security regulations and standards in the cloud due to the complexities of cloud environments and the shared responsibility model.
Insider Threats and Privileged Access
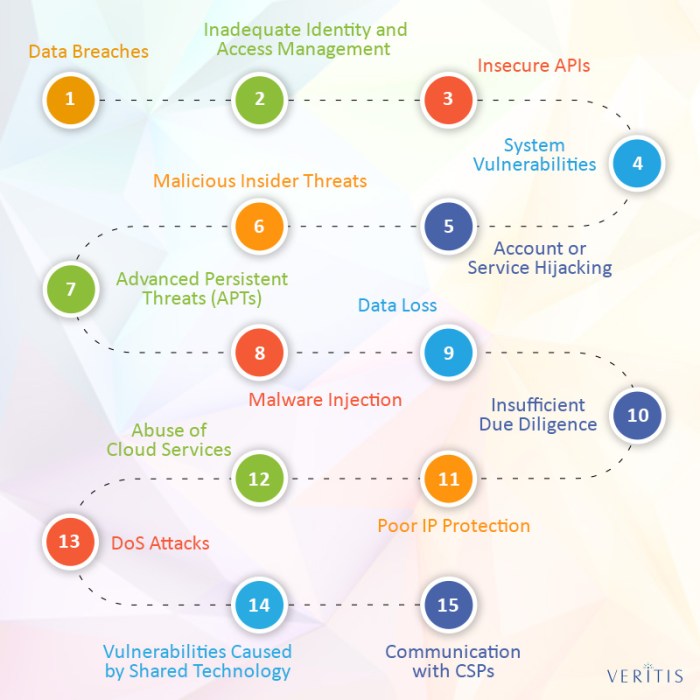
Insider threats and privileged access pose significant risks to cloud computing environments. Malicious insiders with elevated privileges can exploit their access to sensitive data and systems, leading to data breaches, unauthorized modifications, and disruptions. Mitigating these risks requires a multi-layered approach involving role-based access control (RBAC), multi-factor authentication (MFA), continuous monitoring, and regular security audits.
RBAC and Access Control
Role-based access control (RBAC) is a security model that assigns users specific roles and permissions based on their job functions and responsibilities. This approach minimizes the risk of unauthorized access by granting users only the privileges necessary to perform their tasks.
RBAC can be implemented through cloud platforms’ built-in access control mechanisms or third-party solutions.
MFA and Strong Authentication
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of identification before accessing sensitive data or systems. This can include a combination of passwords, biometrics, or one-time passwords (OTPs) sent to a user’s mobile device.
MFA significantly reduces the risk of unauthorized access, even if a user’s credentials are compromised.
Continuous Monitoring and Logging
Continuous monitoring and logging are essential for detecting and responding to insider threats promptly. Cloud platforms typically provide robust logging capabilities that allow organizations to track user activities, system events, and security incidents. By analyzing these logs, security teams can identify anomalous behavior, potential threats, and suspicious activities that may indicate insider misconduct.
Regular Security Audits
Regular security audits are crucial for assessing the effectiveness of cloud security measures and identifying vulnerabilities that could be exploited by insider threats. These audits should be conducted by qualified security professionals who can evaluate the organization’s cloud infrastructure, access controls, and security policies.
Audits should also include reviews of user activity logs and privileged access logs to identify any suspicious patterns or unauthorized activities.
Case Study: Insider Threat at a Cloud Service Provider
In 2020, a cloud service provider experienced a data breach caused by an insider threat. A disgruntled employee with privileged access to customer data stole sensitive information and sold it to a competitor. The breach resulted in the exposure of personal and financial data of millions of customers, leading to reputational damage and legal consequences for the cloud service provider.
Case Study: Insider Threat at a Financial Institution
In 2021, a financial institution fell victim to an insider threat when an employee with access to the institution’s cloud-based banking system manipulated financial records to embezzle funds. The employee exploited a vulnerability in the institution’s RBAC system to gain unauthorized access to customer accounts and transfer funds to personal accounts.
The incident resulted in financial losses and a loss of trust among customers.
Compliance and Regulatory Issues
In cloud computing, compliance and regulatory requirements play a pivotal role in ensuring the security and integrity of data and systems. Adhering to these requirements is essential for organizations to maintain trust, avoid legal ramifications, and safeguard sensitive information.
Key compliance standards and regulations related to cloud security include:
Health Insurance Portability and Accountability Act (HIPAA)
- HIPAA is a comprehensive federal law that sets standards for protecting sensitive patient health information (PHI) in the United States.
- Cloud providers must implement robust security measures to safeguard PHI, such as encryption, access controls, and regular security audits.
Payment Card Industry Data Security Standard (PCI DSS)
- PCI DSS is a set of security standards designed to protect cardholder data in payment processing systems.
- Cloud providers that handle credit card information must comply with PCI DSS requirements to ensure the confidentiality and integrity of cardholder data.
General Data Protection Regulation (GDPR)
- GDPR is a comprehensive data protection regulation in the European Union that sets stringent requirements for the collection, processing, and transfer of personal data.
- Cloud providers operating in the EU or handling personal data of EU citizens must comply with GDPR to protect the rights and privacy of individuals.
Best practices for ensuring compliance with regulatory requirements in cloud environments include:
- Conduct thorough due diligence on cloud providers to assess their security measures and compliance track record.
- Enter into a comprehensive service level agreement (SLA) with the cloud provider that clearly Artikels security responsibilities and compliance obligations.
- Implement additional security measures, such as encryption, access controls, and monitoring, to enhance the security of data and systems in the cloud.
- Regularly review and update security policies and procedures to stay abreast of evolving regulatory requirements and industry best practices.
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
In the realm of cloud computing, Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks pose significant security risks, threatening the availability and accessibility of cloud services. These attacks aim to overwhelm and disrupt the targeted service by flooding it with excessive traffic, rendering it incapable of responding to legitimate requests.
The consequences of DoS and DDoS attacks can be severe, leading to financial losses, reputational damage, and service disruptions. Cloud-based applications and services, due to their inherent connectivity and reliance on internet infrastructure, are particularly vulnerable to these attacks.
Mitigation Strategies and Best Practices
To safeguard against DoS and DDoS attacks in cloud environments, a comprehensive approach is required, encompassing proactive measures and responsive actions. These include:
- Network Security Controls: Implementing robust network security measures, such as firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS), can help detect and mitigate malicious traffic.
- Rate Limiting and Load Balancing: Employing rate-limiting techniques and load balancing mechanisms can help absorb and distribute traffic surges, reducing the impact of DoS attacks.
- DDoS Mitigation Services: Utilizing specialized DDoS mitigation services provided by cloud providers or third-party vendors can offer dedicated protection against DDoS attacks.
- Regular Security Audits and Updates: Continuously monitoring and auditing cloud infrastructure and applications for vulnerabilities, as well as promptly applying security patches and updates, can help prevent successful DoS and DDoS attacks.
Notable DoS and DDoS Attacks on Cloud Platforms
The history of cloud computing is marked by several notable DoS and DDoS attacks that targeted prominent cloud platforms and services. These attacks serve as reminders of the evolving threat landscape and the need for robust security measures:
- Amazon Web Services (AWS) DDoS Attack (2020): In February 2020, AWS experienced a massive DDoS attack that peaked at 2.3 terabits per second (Tbps), targeting the company’s Elastic Load Balancing (ELB) service. This attack disrupted several high-profile websites and services hosted on AWS.
- Google Cloud Platform (GCP) DDoS Attack (2017): In 2017, Google Cloud Platform (GCP) faced a record-breaking DDoS attack that reached a peak of 2.54 Tbps. The attack targeted Google’s Cloud Armor service, which is designed to protect against DDoS attacks, demonstrating the evolving capabilities of attackers.
- Microsoft Azure DDoS Attack (2018): In 2018, Microsoft Azure was subjected to a DDoS attack that reached a peak of 1.7 Tbps, targeting Azure’s Content Delivery Network (CDN) service. This attack highlighted the importance of CDN security and the need for cloud providers to invest in robust DDoS mitigation capabilities.
Misconfigurations and Human Error
Misconfigurations and human error play a significant role in cloud security breaches. Cloud environments are complex, and managing them securely requires a high level of expertise and attention to detail. Misconfigurations can arise from various factors, such as incorrect settings, improper access controls, or outdated software.
Human error can also lead to security vulnerabilities, such as inadvertently granting excessive permissions or mishandling sensitive data.
Common Examples of Misconfigurations
Some common examples of misconfigurations that can lead to security vulnerabilities in cloud environments include:
- Leaving default passwords or keys unchanged.
- Granting excessive permissions to users or applications.
- Misconfiguring security groups or network access control lists.
- Failing to implement encryption for sensitive data.
- Using outdated or unpatched software.
Best Practices for Minimizing Misconfigurations and Human Error
To minimize misconfigurations and reduce the risk of human error in cloud security, organizations should adopt the following best practices:
- Implement strong identity and access management (IAM) controls, including multi-factor authentication and role-based access control.
- Regularly review and update cloud configurations to ensure they are secure and compliant.
- Use automation tools to detect and correct misconfigurations.
- Provide comprehensive security training and awareness programs for cloud users.
- Conduct regular security audits and penetration testing to identify and address vulnerabilities.
Cloud Supply Chain Security
The cloud supply chain involves a network of interconnected entities, including cloud providers, third-party software vendors, service providers, and infrastructure providers, all working together to deliver cloud services. Each component of the supply chain introduces potential security risks that organizations need to address.
The security of the cloud supply chain is of paramount importance as it directly impacts the security of the cloud services and the data stored within them. A breach in the cloud supply chain can have far-reaching consequences, leading to data loss, unauthorized access, and disruption of services.
Due Diligence and Risk Assessment
Organizations must conduct thorough due diligence and risk assessments when selecting cloud providers and partners. This involves evaluating the security practices, policies, and controls of the potential partners to ensure they align with the organization’s security requirements and industry best practices.
- Review Security Policies and Standards: Assess the cloud provider’s security policies, compliance certifications, and adherence to industry standards such as ISO 27001, SOC 2, and HIPAA.
- Evaluate Security Controls: Examine the technical security controls implemented by the cloud provider, including encryption, access controls, network security, and incident response capabilities.
- Assess Third-Party Risk: Evaluate the security practices of third-party software vendors, service providers, and infrastructure providers integrated with the cloud platform.
- Conduct Regular Audits and Reviews: Regularly audit and review the security practices and controls of cloud providers and partners to ensure ongoing compliance and adherence to security standards.
Managing and Securing the Cloud Supply Chain
Once cloud providers and partners are selected, organizations must implement measures to manage and secure the cloud supply chain effectively.
- Establish Clear Contracts and SLAs: Define clear contractual agreements and service-level agreements (SLAs) that Artikel the security responsibilities and expectations of each party involved in the cloud supply chain.
- Implement Continuous Monitoring: Continuously monitor the cloud supply chain for suspicious activities, security incidents, and vulnerabilities. Establish processes for timely detection and response to security threats.
- Enforce Least Privilege Access: Implement the principle of least privilege access to limit the access rights of users and applications to only the resources they need to perform their tasks.
- Educate and Train Personnel: Provide regular security awareness training and education to personnel working with cloud services to ensure they understand their roles and responsibilities in maintaining cloud security.
Data Encryption and Key Management
Data encryption and key management are critical aspects of cloud security, ensuring the confidentiality and integrity of sensitive information stored and processed in the cloud.
Encryption transforms data into an unreadable format, requiring a key to decrypt and access it. Key management involves the generation, storage, and distribution of encryption keys in a secure manner.
Encryption Methods
- Symmetric Encryption: Uses the same key to encrypt and decrypt data. It is computationally efficient but requires secure key distribution and management.
- Asymmetric Encryption: Utilizes a pair of keys
– a public key for encryption and a private key for decryption. It is more secure but computationally intensive.
Key Management Techniques
- Key Rotation: Regularly changing encryption keys to reduce the risk of compromise.
- Key Splitting: Dividing the encryption key into multiple parts, stored in different locations, requiring multiple parties to access the complete key.
- Hardware Security Modules (HSMs): Physical devices dedicated to securely generating, storing, and managing cryptographic keys.
Best Practices
- Encrypt Data at Rest and in Transit: Ensure data is encrypted both when stored in the cloud and during transmission.
- Implement Strong Key Management: Use robust key management techniques, such as key rotation and splitting, to protect encryption keys.
- Use Cloud-Native Encryption Services: Leverage encryption services provided by cloud providers, which are designed for ease of use and scalability.
- Educate Employees on Encryption: Train employees on the importance of encryption and key management to prevent security breaches.
Continuous Monitoring and Incident Response
Continuous monitoring and incident response are crucial aspects of cloud security, ensuring the prompt detection and mitigation of security incidents. Effective security monitoring involves collecting and analyzing security-related data in real-time to identify potential threats, suspicious activities, and security breaches.
Incident response plans Artikel the steps to be taken when a security incident occurs, including containment, eradication, recovery, and lessons learned.
Security Monitoring Tools and Techniques
Security monitoring tools and techniques play a vital role in detecting and responding to security incidents in the cloud. These tools include:
- Log Management and Analysis: Centralized log management and analysis systems collect and analyze logs from various cloud resources to identify anomalies and potential security incidents.
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): IDS and IPS monitor network traffic for suspicious activities and can block malicious traffic in real-time.
- Vulnerability Scanning: Vulnerability scanning tools identify known vulnerabilities in cloud resources, enabling organizations to prioritize patching and remediation efforts.
- Security Information and Event Management (SIEM) Systems: SIEM systems aggregate security-related data from various sources, providing a centralized view of security events and enabling correlation and analysis.
Summary

The ever-evolving nature of cloud computing demands a proactive approach to security. Organizations must continuously assess and mitigate risks, implementing robust security measures and adhering to industry best practices. By adopting a comprehensive security strategy that addresses the unique challenges of the cloud, businesses can harness the full potential of cloud computing while safeguarding their valuable assets.